442018 For example crypto mining traffic is periodic though malware writers will try to disguise the regular nature of the communication by for example randomizing the intervals. Once a device is infected with the malicious code it begins using the CPU and memory resources of its hardware host to collectively mine a designated cryptocurrency.
 Analysis Break Even Point Of Mining Bitcoin Is Around 2 400 Technology News World What Is Bitcoin Mining Blockchain Cryptocurrency
Analysis Break Even Point Of Mining Bitcoin Is Around 2 400 Technology News World What Is Bitcoin Mining Blockchain Cryptocurrency
You click on a malicious link in an email and it loads cryptomining code directly onto your computer.

How does crypto mining malware work. Criminals are turning to cryptojacking malware to do the work for them. Once activated such a malicious file can affect individuals as much as large enterprises that rely their operations on networks of countless servers. Basically cryptocurrency mining malware stealthily hijacks devices like computers or phones and steals their resources for mining cryptocurrencies.
What does the crypto-jacking malware do. The most popular method of distribution is via infected websites. This crypto-mining Android malware.
This block of data then gets stored on the blockchain and a new block is ready to be solved. This is important because it makes it extremely difficult for anyone to forge a transaction but easy to verify transactions on the blockchain. 3242021 Cryptocurrency-mining malware also known as crypto-jacking is malicious software that penetrates peoples devices eg smartphones tablets computers or even servers to secretly mine cryptocurrency without users explicit permission.
The same general recommendations for avoiding regular viruses apply here too. 3162021 A more unscrupulous mining method involves cryptocurrency mining malware. Crypto mining using malware is a completely different matter.
Threat actors do not build a dedicated crypto-mining network. This malware-based crypto-mining technique has developed in the past few years in parallel to the growth in popularity of cryptocurrencies. It involves hard work done by computers and results in a slow accumulation of resources just like mining.
1142020 Proof-of-Work is a crypto mining protocol that defines an extensive mathematical computation that needs to be performed in order to create a new block for the blockchain. It can quickly wear down a machine causes slowdowns and costs electricity. 1192021 Mining in the crypto world is the process of keeping blockchain data in check.
In a nutshell this is crypto mining. As miners increased by number the complexities of crypto calculations increased with it hashrates being the variable which is the speed at which the crypto puzzles are calculated and deliver. The cybercriminals use different ways to smuggle it onto the computers of their victims.
The term crypto mining means gaining cryptocurrencies by solving cryptographic equations through the use of computers. This method uses malware specially designed for mining cryptocurrencies. Crypto mining malware spreads just like any other viruses.
One method works like classic malware. They may be downloaded from unofficial software repositories sent through peer-to-peer file-sharing services sent by email as apparently normal documents and so on. Mining difficulty controls the rate of coin creation.
Dishonest miners distribute malware throughout the world to infect unsuspecting users. 10162020 What Is Crypto Mining. The miner or mining pool who finds a block first gets the reward as long as their work is confirmed as valid across the rest of the network.
Why it is such a menace and where its going next. Once your computer is infected the cryptojacker starts working around the clock to mine cryptocurrency while staying hidden in. Cryptojacking malware works by secretly using the resources of your computer to mine cryptocurrencies for the hackers who control them.
Dexphot is advanced but the cryptomining malware threat often takes second place to that of data breaches. This process involves validating data blocks and adding transaction records to a public record ledger known as a blockchain. 1252019 Once in a computer system cryptomining malware can secretly use the devices resources to mine cryptocurrency sending the reward back to the cybercriminals.
Download programs only from trustworthy official sources dont open links or.
 Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog
Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog
 Minix Bitcoin Mining Psd Template Ad Bitcoin Minix Mining Template Malwareanalysis Bitcoin Mining Bitcoin Mining Hardware Bitcoin
Minix Bitcoin Mining Psd Template Ad Bitcoin Minix Mining Template Malwareanalysis Bitcoin Mining Bitcoin Mining Hardware Bitcoin
 Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog
Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog
 New Free Mining Site Best Free Bitcoin Mining Earn Free Bitcoin Tradingbitcoins Free Bitcoin Mining Bitcoin Mining Bitcoin Mining Software
New Free Mining Site Best Free Bitcoin Mining Earn Free Bitcoin Tradingbitcoins Free Bitcoin Mining Bitcoin Mining Bitcoin Mining Software
 Earn 300 In Bitcoin Every Month New Free Bitcoin Mining Site 2019 No Investment Free Bitcoin Mining Bitcoin Mining What Is Bitcoin Mining
Earn 300 In Bitcoin Every Month New Free Bitcoin Mining Site 2019 No Investment Free Bitcoin Mining Bitcoin Mining What Is Bitcoin Mining
 2800w 90 Plus 91 Btc Eth Mining Power Supply 12 6 Gpu Bitcoin Ethereum Miner Power Supply Graphic Card Crypto Mining
2800w 90 Plus 91 Btc Eth Mining Power Supply 12 6 Gpu Bitcoin Ethereum Miner Power Supply Graphic Card Crypto Mining
 Free Bitcoin Miner For Android Game Be A Miner Bitcoin Hunter Manage Bitcoins Mining Rig Composition Best Amazing Profit Miner Miningsimulator
Free Bitcoin Miner For Android Game Be A Miner Bitcoin Hunter Manage Bitcoins Mining Rig Composition Best Amazing Profit Miner Miningsimulator
 Hot New 100 Ghs Mining Free Btc Cloud Mining Site Bitcoin Mining Cloud Mining Crypto Mining Bitcoin Mining
Hot New 100 Ghs Mining Free Btc Cloud Mining Site Bitcoin Mining Cloud Mining Crypto Mining Bitcoin Mining
 Https Cointiply Com R Reyjd Bitcoin Mining Site Not Accept Deposit Only Withdraw No Risk Have Good G Bitcoin Mining What Is Bitcoin Mining Bitcoin
Https Cointiply Com R Reyjd Bitcoin Mining Site Not Accept Deposit Only Withdraw No Risk Have Good G Bitcoin Mining What Is Bitcoin Mining Bitcoin
 2017 Bitcoin Leaves A Mark In The History Ecoin4dummies Com What Is Bitcoin Mining Blockchain Cryptocurrency
2017 Bitcoin Leaves A Mark In The History Ecoin4dummies Com What Is Bitcoin Mining Blockchain Cryptocurrency
 Cryptojacking Mining Malware On Crypto Currency With Xmrig
Cryptojacking Mining Malware On Crypto Currency With Xmrig
 Pin On Security News Eidhseis Asfaleias
Pin On Security News Eidhseis Asfaleias
 Antminer S9 14th S Bitcoin S9 Miner Mining Brand New Bitcoin Miner S9 Antminer With Power Supply 14t Bitcoin S Bitcoin Mining Bitcoin What Is Bitcoin Mining
Antminer S9 14th S Bitcoin S9 Miner Mining Brand New Bitcoin Miner S9 Antminer With Power Supply 14t Bitcoin S Bitcoin Mining Bitcoin What Is Bitcoin Mining
 What Is Malicious Cryptocurrency Mining History And Prevention
What Is Malicious Cryptocurrency Mining History And Prevention
 Okex Pool Among Top 5 Mining Pools Charts Future Path For The Industry Https Thecryptoreport Com Okex Pool Amon Ethereum Mining Crypto Mining Cryptocurrency
Okex Pool Among Top 5 Mining Pools Charts Future Path For The Industry Https Thecryptoreport Com Okex Pool Amon Ethereum Mining Crypto Mining Cryptocurrency
 Bitcoin Firefox Plans To Block Crypto Mining Malware In Future Releases Crypto Mining Investing In Cryptocurrency What Is Bitcoin Mining
Bitcoin Firefox Plans To Block Crypto Mining Malware In Future Releases Crypto Mining Investing In Cryptocurrency What Is Bitcoin Mining
 What Is Cryptomining Malware Webopedia
What Is Cryptomining Malware Webopedia
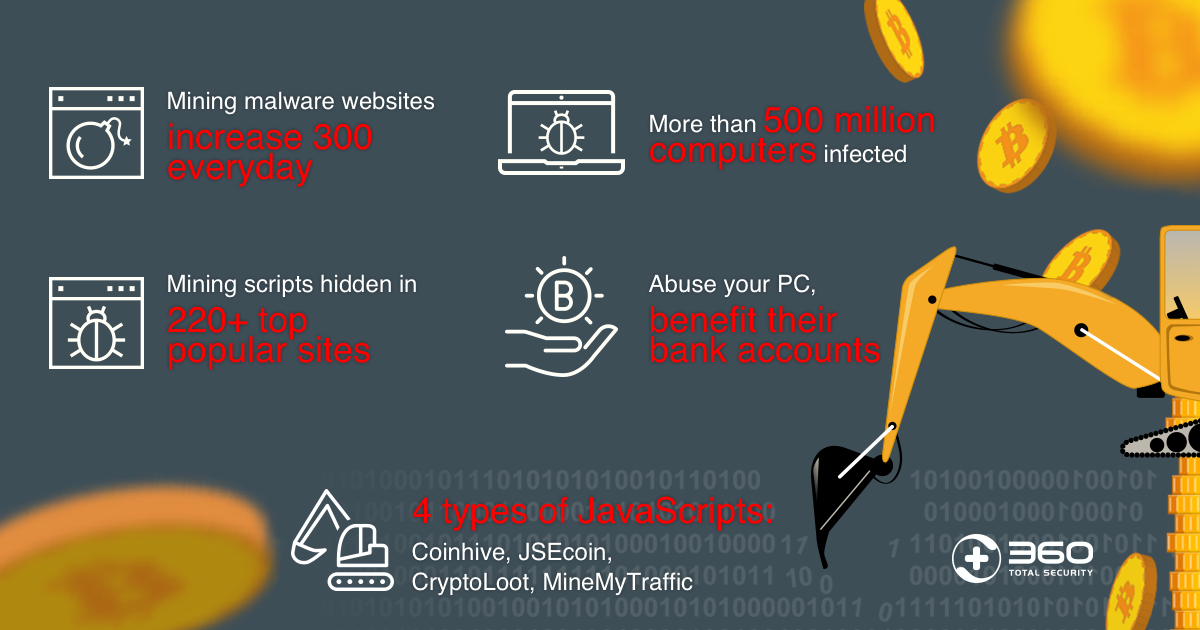 Security Notice Cryptocurrency Mining Malware Rapidly Increasing
Security Notice Cryptocurrency Mining Malware Rapidly Increasing
 Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog
Is Cryptocurrency Mining Malware The New Adware Emsisoft Security Blog